Lync, Forefront, Cisco, etc...
vendredi 2 novembre 2012
Lync 2013 - List CAL Usage
Hi,
This script returns information about client license usage in your organization since the first user connection. Your topology has to include a monitoring server.
#Get Monitoring Instance
$SQLSERVICE=get-csservice | ? {$_.Role -eq "MonitoringDatabase" }
if ($SQLSERVICE -eq $null) { exit }
$SQLINSTANCE = $SQLSERVICE.poolfqdn + "\" + $SQLSERVICE.SqlInstanceName
#Get CALs Usage
$plus=Get-CsClientAccessLicense -MonitoringDatabase $SQLINSTANCE -LicenseName plus -LicenseBasedType Userbased -StartDate 01/01/2012 | ? {$_.IpAddress -match ".+"}
$standard=Get-CsClientAccessLicense -MonitoringDatabase $SQLINSTANCE -LicenseName standard -LicenseBasedType Userbased -StartDate 01/01/2012 | ? {$_.IpAddress -match ".+"}
$enterprise=Get-CsClientAccessLicense -MonitoringDatabase $SQLINSTANCE -LicenseName enterprise -LicenseBasedType Userbased -StartDate 01/01/2012 | ? {$_.IpAddress -match ".+"}
#List Usage
write-host Your organization uses $standard.count Standard Lync CALs"," $enterprise.count Enterprise Lync CALs and $plus.count Plus Lync CALs
Tweeter
mercredi 12 septembre 2012
DirectAccess 2012 RTM–Epic Fail
Hello,
Today, I installed a DlrectAccess PoC on 2012 RTM. I prepared every thing, NLS, PKI, Firewalling, features, everything! I prepared my installation script and launch it!
First line : Install-RemoteAccess ….
The term 'Install-RemoteAccess' is not recognized as the name of a cmdlet
Hum weird…. And via GUI?? File C:\Windows\system32\RAMgmtUI.exe cannot be located

Ok.. and now? Do i forget something?
EDIT : YES!!! With the install-windowsFeature, don't forget -includemanagementtools....
Tweeter
dimanche 9 septembre 2012
Lync 2013, IPv6 and Directaccess
Hi everyone,
This is my first post about Lync and my last about Directaccess
With Lync 2013 Preview, ipv6 is fully supported, so directaccess should work with Lync. Let’s check!
Firstly, we need to configure the lync topology. There is only one standard front-end server.
My sip domain is labda.local. Directaccess clients are configured to send every packet to labda.local domain in the IPsec tunnel.

My environment is full ipv6 so I disable IPv4 and enable IPv6 in the topology builder.

I activate the enterprise voice and the conferencing service on this server.
Ok now let’s check that Lync 2013 is working on the client!
Firstly, the dns resolution for the automatic configuration (2abc::11 is the dns server on my nrpt table, it’s the directaccess server):

Great, now let’s connect the lync client.

And a call? (i have only one user

And a meet now?

So every thing is working is IPV6. Even Location services!

Even location services? Maybe not… Let’s check on the client…

No proposition, what is my ipv6 address?

Mmmm, very weird… Snooper is my friend!! So firstly, turn on tracing on my client
I get a log file on the client, stored in
%userprofile%\AppData\Local\Microsoft\Office\15.0\Lync\Tracing
Let’s analyze the log with snooper, and search the keyword subnet


So the subnet information sent by the client contains the ipv4 address, that’s why i don’t get my location information. So Lis doesn’t work with directaccess ip. I thing that it’s a normal behavior, we cannot predict where my client will be with directaccess. The best location with directaccess is somewhere!
Bye
Tweeter
samedi 8 septembre 2012
Windows 8 and DirectAccess 2012
Hi everyone,
As you know, with windows 7 and directaccess, a tool is necessary to determine easily if the directaccess connection is working. The tool enables the end user to disable the directaccess connection if it’s not working. It enables the end user to send information about the connection to the help desk team.

This tool is not necessary with windows 8! This functionality is included by default.
How do we configure it?
On the directaccess server with the command :Set-DAClientExperienceConfiguration
What are the parameters?
Firstly, we need to choose the Gpo where these settings will be stored: –policystore
-Friendlyname : Specifies the name of the DirectAccess deployment to be shown in the client computer user interface.
-CorporateResources : Configures the connectivity tests that DirectAccess client computers use to determine connectivity.
-IPsecTunnelEndpoints : Configures the IPsec tunnel endpoints to use for DirectAccess. Client computers use this information to verify the availability of the DirectAccess servers and present that information to the user.
-PreferLocalNamesAllowed: Controls if users can disconnect DirectAccess.
-SupportEmail: Configures the email address displayed in the user interface for users to send logs and requests for assistance.
Together :

Verify the Gpo

Ok, now let’s check on the client!

The settinga are deployed. Let’s check the behaviour. The connection name is well configured and the user can disconnect the tunnel, so disable the nrpt Table

Right-click, view connection properties

We see the connection status, we can send the logs by email and we can view the logs

The logs have been improved!

The information are sorted. I can see that i can’t ping my second public ip. (I need to write a rule in my edge firewall
As a conclusion, directaccess rocks!
Tweeter
mercredi 5 septembre 2012
UAG - Appwrap and Change Header
Hi,
I got a problem on UAG some weeks ago.
An application need to use a referer header in the http requests to deliver contents.
The application was published by UAG, but it was not working.
I captured the traffic between the client and the UAG and between the UAG and the application.
The only difference between both requests was a change in the referer header. UAG behaviour is to rewrite the referer header, replacing the host name by the published ip server.
The microsoft support said me to use AppWrap to rewrite (again) the referer Header.
So, We need to rewrite the ip with the host name.
The appwrap syntax was the following :
And that's all!
Bye
Tweeter
I got a problem on UAG some weeks ago.
An application need to use a referer header in the http requests to deliver contents.
The application was published by UAG, but it was not working.
I captured the traffic between the client and the UAG and between the UAG and the application.
The only difference between both requests was a change in the referer header. UAG behaviour is to rewrite the referer header, replacing the host name by the published ip server.
The microsoft support said me to use AppWrap to rewrite (again) the referer Header.
So, We need to rewrite the ip with the host name.
The appwrap syntax was the following :
And that's all!
Bye
Tweeter
lundi 3 septembre 2012
DirectAccess 2012 – Enable NLB
Hey,
So this post will be in English!
In the RAMgmtUI.exe, we enable Load Balancing

And we see a nice message : the length of the prefix used to assign IPv6 addresses to directaccess clients connecting over IP-HTTPS should be 59 bits.

What is our prefix?

The prefix is based on our internal IPV6 prefix : 2abc::/64. I think that the maximum number of Node in a directaccess cluster is 32. Why? 64-59 = 5. 2^5 = 32.
.

For the node 1, the client ipv6 address will be 2abc::FF00::eui-64/64
For the node 2, the client ipv6 address will be 2abc::FF01::eui-64/64
Great. Now, let’s try to activate the NLB! (We need to relaunch the RAMgmtUI.exe so that the wizard takes into account the prefix change).
The wizard is simple. The DIP will become the VIP. We just need to define new DIP for the directaccess server.


Let’s check on the windows 8 client if the directaccess server is still working. The client gets an ipv6 with the iphttpsinterface. And the client resolves an intranet dns record.


Now, we are going to add a new node in powershell. The second node reboots automatically. (but maybe not voluntarily... )

And the GPO? Great the security filtering is automatically updated!

But now, i get nice blue screen on EDGE2

So, i need to format!!!
See you after the formatting
EDIT: I tried again... and got same results whatever if use powershell or GUI... Waiting the final release!! I have to deploy a POC with 2012 RC for a client.(hopfully wihout NLB :) )
Tweeter
jeudi 30 août 2012
Windows Server 2012 - DirectAccess Part 2
Accrochez-vous, il va y avoir de l'IPV6
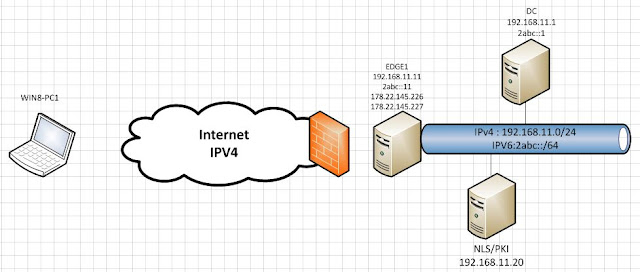
Aujourd'hui, nous allons rajouter un prefix IPV6 dans notre LAN : 2abc::/64
Pour simplifier, le "dernier octet" sera identique au dernier octet de l'ipv4.
Le dc aura l'ip 2abc::1/64
Edge1 aura l'ip 2abc::11/64 (et non pas 2abc::B/64, je simplifie au maximum ;) )
J'ai également supprimer le record ISATAP.
Regardons les différences que cela entraîne.
Déjà dans l'ip obtenu pour les client directaccess. Celle-ci est basée sur le prefix IPv6 en interne. Il vaut donc mieux éviter d'utiliser l'ipv6 monprefix:1000::/64 dans nos reseaux ipv6 sinon il y aura des petits soucis de routage par défaut ;)
S'il n'y a pas d'ipv6 sur le lan du serveur directaccess, le prefix qu'utilise le serveur directaccess pour les ips des clients est base sur l'ip 6to4.
Bien sur, cette fois-ci les résolutions dns sont en IPV6.
Le dns dans la table NRPT pointe sur l'ipv6 interne du serveur et non plus une ipv6 basée sur le prefix 6to4.
Bien sur les gpo ont été mises a jour pour permettre d'ouvrir des tunnels IPSec sur le prefix 2abc::/48
Et voila, c'est tout pour l'ajout d'IPV6!
Tweeter
Aujourd'hui, nous allons rajouter un prefix IPV6 dans notre LAN : 2abc::/64
Pour simplifier, le "dernier octet" sera identique au dernier octet de l'ipv4.
Le dc aura l'ip 2abc::1/64
Edge1 aura l'ip 2abc::11/64 (et non pas 2abc::B/64, je simplifie au maximum ;) )
J'ai également supprimer le record ISATAP.
Regardons les différences que cela entraîne.
Déjà dans l'ip obtenu pour les client directaccess. Celle-ci est basée sur le prefix IPv6 en interne. Il vaut donc mieux éviter d'utiliser l'ipv6 monprefix:1000::/64 dans nos reseaux ipv6 sinon il y aura des petits soucis de routage par défaut ;)
Bien sur, cette fois-ci les résolutions dns sont en IPV6.
Le dns dans la table NRPT pointe sur l'ipv6 interne du serveur et non plus une ipv6 basée sur le prefix 6to4.
Bien sur les gpo ont été mises a jour pour permettre d'ouvrir des tunnels IPSec sur le prefix 2abc::/48
Et voila, c'est tout pour l'ajout d'IPV6!
Tweeter
Inscription à :
Articles (Atom)